In the digital age, data security and system monitoring are of paramount importance. Windows logging plays a crucial role in providing insights into the health, performance, and security of a Windows operating system. This article aims to delve into the fundamentals of Windows logging, explaining its significance, types of logs, and best practices for effective log management.
If you’re experiencing obstacles with The Best Malware Removal Software in 2023, our website offers an in-depth tutorial that walks you through the process step by step.
Exploring the Basics of Windows Logging – Significance, Log Types, and Best Practices
Understanding Windows Logging
Windows logging involves the process of capturing, storing, and analyzing events that occur within the Windows operating system. These events can include security-related activities, system errors, user actions, and application activities. By monitoring and analyzing these logs, system administrators gain valuable insights into the functioning and security of the Windows environment.
Types of Windows Logs
Windows logging encompasses various types of logs, each serving a specific purpose. Here are the primary types of Windows logs:
Event Logs
Event logs are the core component of Windows logging. They capture system events, including security events, application events, and system errors. The Event Viewer utility allows administrators to view and analyze these logs.
Security Logs
Security logs focus on recording security-related events, such as failed logins, account lockouts, and privilege usage. They provide vital information for detecting and investigating potential security breaches.
Application Logs
Application logs record events generated by applications running on the Windows system. These logs help diagnose and troubleshoot application-specific issues, such as crashes, errors, or unexpected behavior.
System Logs
System logs capture events related to the operating system’s core functionality. These logs monitor system startup, shutdown, driver installations, and hardware changes.
Setup Logs
Setup logs document the installation and configuration of software and system components. They aid in troubleshooting issues during software installation or system setup processes.
Importance of Windows Logging
Windows logging offers several key benefits that contribute to the overall health and security of a system:
Security Monitoring
By analyzing security logs, administrators can detect and respond to potential security threats promptly. Unusual login attempts, changes to system privileges, or suspicious activities can be identified, enabling administrators to take necessary actions to mitigate risks.
Troubleshooting and Diagnostics
Windows logs serve as a valuable resource for diagnosing and troubleshooting system issues. Application logs can provide insights into software crashes, while system logs can pinpoint hardware or driver-related problems. Analyzing these logs expedites the resolution of technical issues.
Performance Analysis
Log analysis can aid in identifying system bottlenecks and performance issues. By monitoring performance-related logs, administrators can optimize system performance, enhance user experience, and ensure efficient resource utilization.
Compliance and Auditing
Windows logging is crucial for meeting compliance requirements and facilitating auditing processes. Organizations often need to demonstrate adherence to specific regulations or internal policies. Windows logs provide a detailed record of system activities that can be reviewed during audits.
Best Practices for Windows Log Management
To leverage the full potential of Windows logging, following best practices for log management is essential:
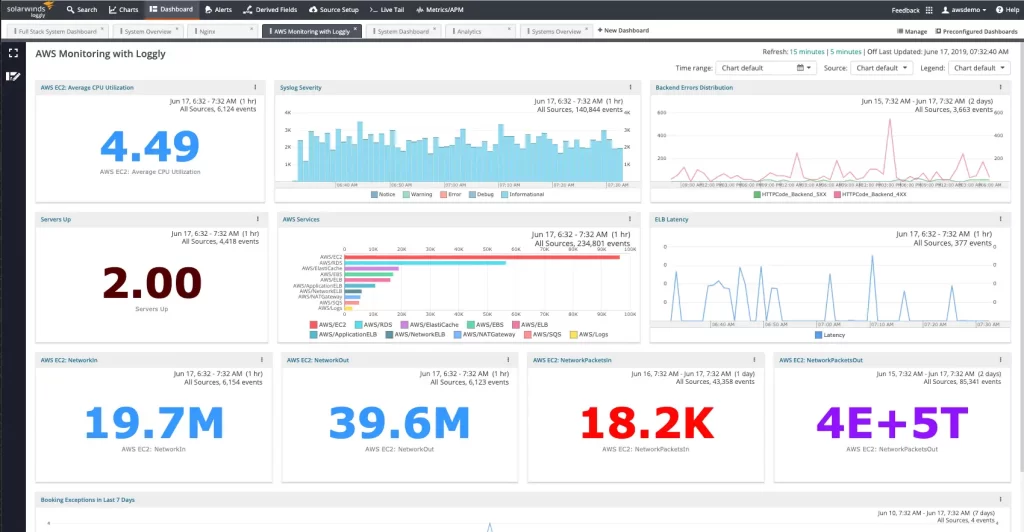
Enable and Configure Appropriate Logging
Ensure that logging is enabled on all relevant Windows systems and configure the appropriate log settings. Determine the log retention period based on your organization’s requirements and comply with any regulatory guidelines.
Centralized Log Collection
Implement a centralized log collection mechanism to gather logs from multiple Windows systems. This simplifies log analysis, enhances visibility, and facilitates correlation of events for better security monitoring.
Regular Log Analysis
Allocate time for regular log analysis to proactively identify security threats, system errors, and performance issues. Utilize log analysis tools or security information and event management (SIEM) solutions to automate log analysis processes.
Set Up Alerts
Configure alerts for critical log events to receive notifications for potential security incidents or system anomalies. Timely alerts enable prompt investigation and mitigation actions, reducing the impact of security breaches or system failures.
Monitor Log Integrity
Ensure the integrity of logs by implementing measures to protect them from unauthorized modification or deletion. Consider utilizing file integrity monitoring (FIM) solutions or log integrity verification mechanisms.
Regular Backup and Archiving
Regularly back up and archive logs to preserve historical data. This practice aids in compliance, forensics, and retrospective analysis in the event of security incidents or system failures.
Conclusion
Windows logging is an indispensable aspect of maintaining the security, stability, and performance of a Windows operating system. By understanding the types of logs, the significance of logging, and following best practices for log management, organizations can ensure a robust and secure computing environment. Windows logs provide valuable insights into system activities, aiding in troubleshooting, performance optimization, security monitoring, and compliance requirements. Prioritizing effective log management can significantly enhance the overall operational efficiency and security posture of Windows-based systems.